시스템/쿠버네티스
[쿠버네티스] 젠킨스 플러그인 설치 & 깃랩연동
cbwstar
2024. 1. 12. 14:51
728x90
반응형
1. 젠킨스 플러그인 설치
1. Bitbucket Pipeline for Blue Ocean
2. Dashboard for Blue Ocean
3. Personalization for Blue Ocean
4. Display URL for Blue Ocean
5. Server Sent Events (SSE) Gateway
6. Events API for Blue Ocean
7. Blue Ocean Pipeline Editor
8. i18n for Blue Ocean
9. Autofavorite for Blue Ocean
10. Blue Ocean
11. NodeJS
12. GitLab
13. Generic Webhook Trigger
14. Gitlab Authentication
15. Gitlab API
16. GitLab Branch Source
17. Gitlab Merge Request Builder
18. Config File Provider
19. Docker
20. Docker Pipeline
21. docker-build-step
22. SSH Agent
23. Post build task2. 깃랩 연결
1) 깃랩 액세스 토큰 발행

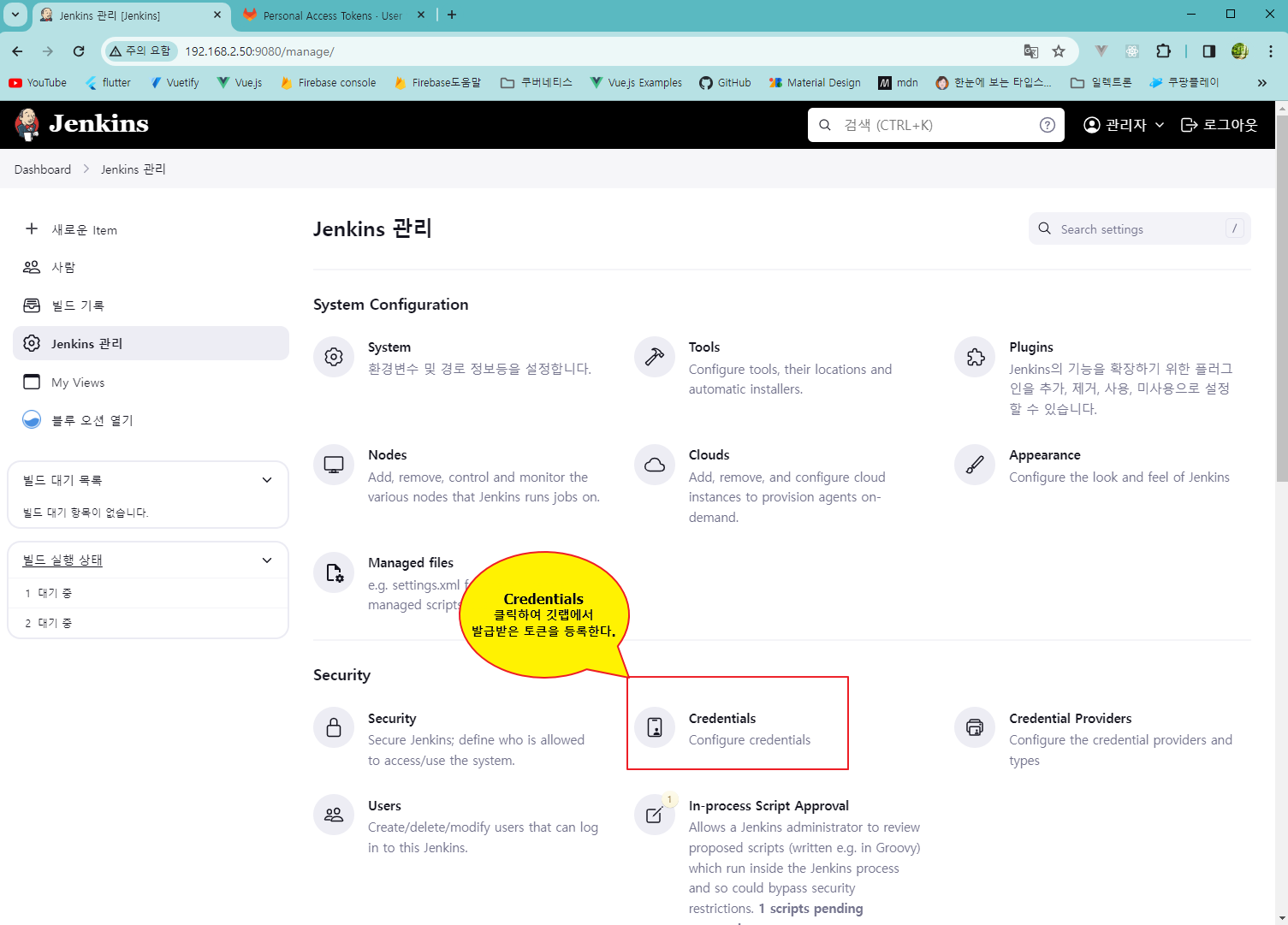
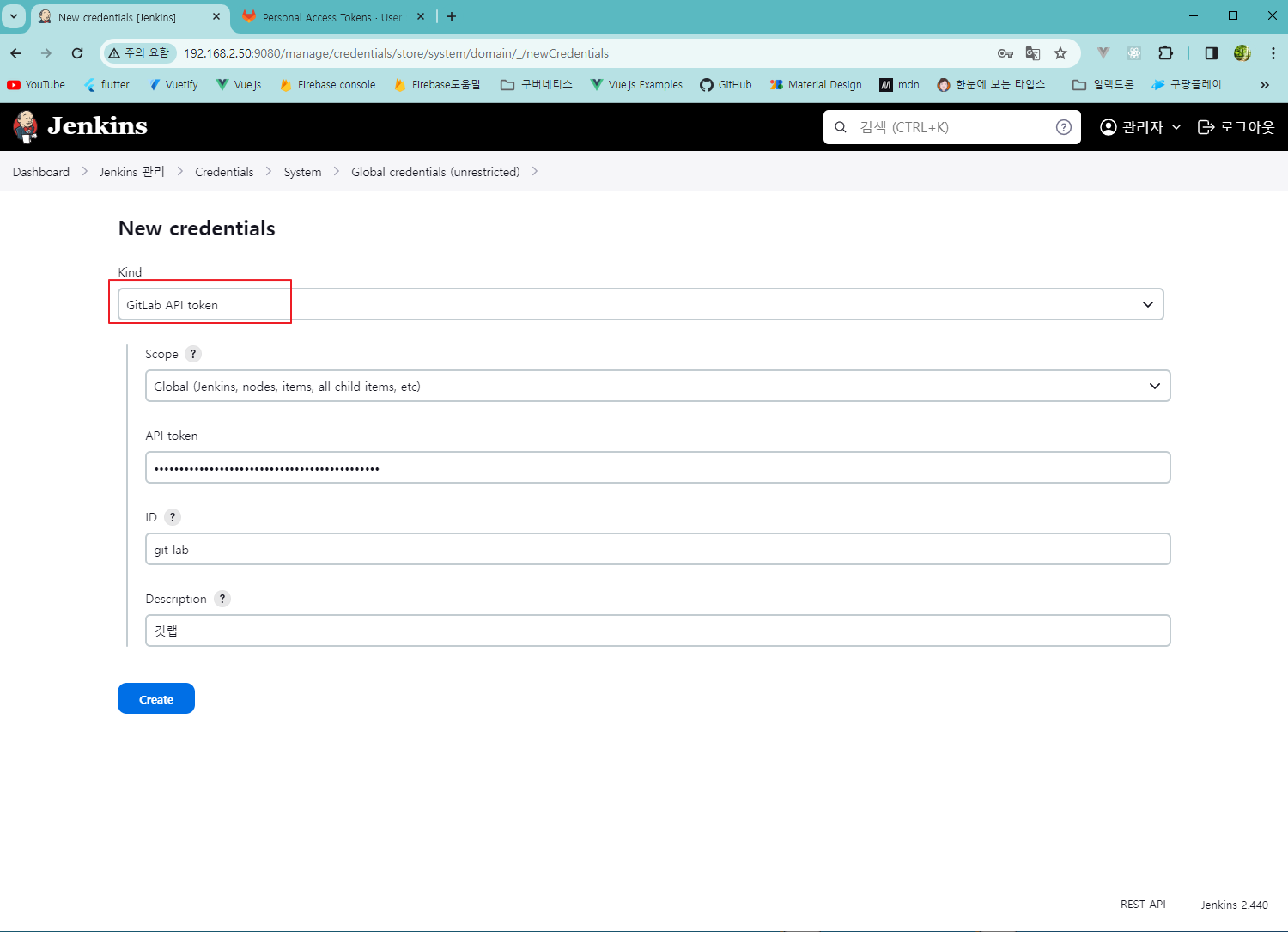
2) 젠킨스 토큰 등록
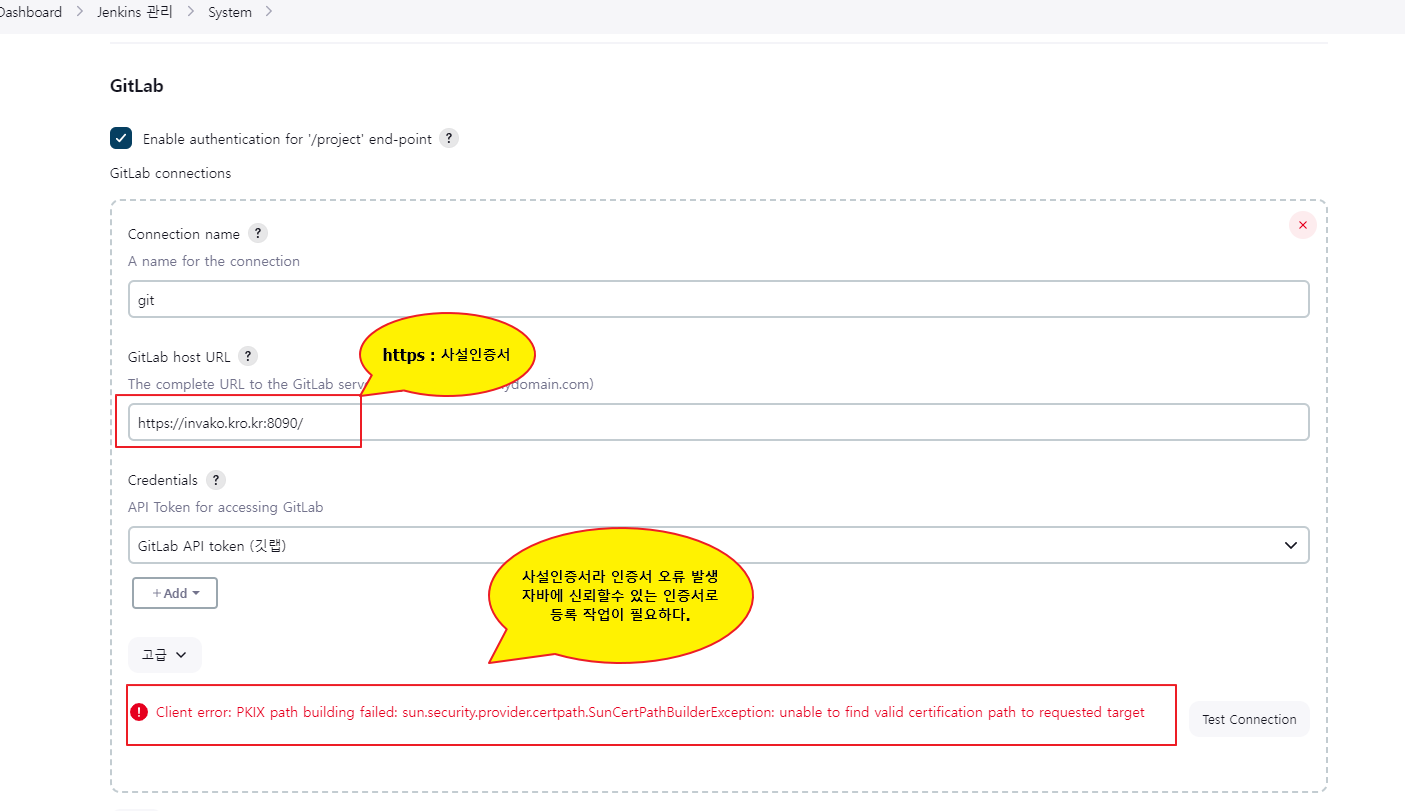
3. 자바 인증서 오류 처리
mkdir -p /var/jenkins_home/cert
cd /var/jenkins_home/cert
curl -O https://gist.githubusercontent.com/lesstif/cd26f57b7cfd2cd55241b20e05b5cd93/raw/InstallCert.java
javac InstallCert.java
root@jenkins:/var/jenkins_home/cert# java -cp ./ InstallCert invako.kro.kr:8090
Loading KeyStore /opt/java/openjdk/lib/security/cacerts...
Opening connection to invako.kro.kr:8090...
Starting SSL handshake...
javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at java.base/sun.security.ssl.Alert.createSSLException(Alert.java:131)
at java.base/sun.security.ssl.TransportContext.fatal(TransportContext.java:360)
at java.base/sun.security.ssl.TransportContext.fatal(TransportContext.java:303)
at java.base/sun.security.ssl.TransportContext.fatal(TransportContext.java:298)
at java.base/sun.security.ssl.CertificateMessage$T13CertificateConsumer.checkServerCerts(CertificateMessage.java:1357)
at java.base/sun.security.ssl.CertificateMessage$T13CertificateConsumer.onConsumeCertificate(CertificateMessage.java:1232)
at java.base/sun.security.ssl.CertificateMessage$T13CertificateConsumer.consume(CertificateMessage.java:1175)
at java.base/sun.security.ssl.SSLHandshake.consume(SSLHandshake.java:392)
at java.base/sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:443)
at java.base/sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:421)
at java.base/sun.security.ssl.TransportContext.dispatch(TransportContext.java:183)
at java.base/sun.security.ssl.SSLTransport.decode(SSLTransport.java:172)
at java.base/sun.security.ssl.SSLSocketImpl.decode(SSLSocketImpl.java:1511)
at java.base/sun.security.ssl.SSLSocketImpl.readHandshakeRecord(SSLSocketImpl.java:1421)
at java.base/sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:456)
at java.base/sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:427)
at InstallCert.main(InstallCert.java:116)
Caused by: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at java.base/sun.security.validator.PKIXValidator.doBuild(PKIXValidator.java:439)
at java.base/sun.security.validator.PKIXValidator.engineValidate(PKIXValidator.java:306)
at java.base/sun.security.validator.Validator.validate(Validator.java:264)
at java.base/sun.security.ssl.X509TrustManagerImpl.validate(X509TrustManagerImpl.java:313)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:233)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:110)
at InstallCert$SavingTrustManager.checkServerTrusted(InstallCert.java:199)
at java.base/sun.security.ssl.AbstractTrustManagerWrapper.checkServerTrusted(SSLContextImpl.java:1492)
at java.base/sun.security.ssl.CertificateMessage$T13CertificateConsumer.checkServerCerts(CertificateMessage.java:1341)
... 12 more
Caused by: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at java.base/sun.security.provider.certpath.SunCertPathBuilder.build(SunCertPathBuilder.java:148)
at java.base/sun.security.provider.certpath.SunCertPathBuilder.engineBuild(SunCertPathBuilder.java:129)
at java.base/java.security.cert.CertPathBuilder.build(CertPathBuilder.java:297)
at java.base/sun.security.validator.PKIXValidator.doBuild(PKIXValidator.java:434)
... 20 more
Server sent 1 certificate(s):
1 Subject CN=invako.kro.kr, OU=Personal, O=invako, L=Osong, ST=South, C=CN
Issuer CN=invako.kro.kr, OU=Personal, O=invako, L=Osong, ST=Osong, C=CN
sha1 50 e0 9d 5d d1 e0 98 18 bb e8 3c 82 7d 82 7e b8 af 8a 30 86
md5 3f 8a 70 cf d3 6a 36 1d b1 ca 23 7a 8e dd 0d 60
Enter certificate to add to trusted keystore or 'q' to quit: [1]1번 선택
Algorithm: [SHA512withRSA]
Signature:
0000: B1 58 36 ED 91 98 A8 0D 1D 01 5E E9 A3 0F 86 41 .X6.......^....A
0010: A3 21 78 39 15 E1 68 3B 8C F2 0B B6 D4 53 74 3B .!x9..h;.....St;
0020: 51 AC E3 41 8B 2E 5D 7D 4A B7 78 EC A7 CA 88 05 Q..A..].J.x.....
0030: 36 25 96 CA 54 1F A6 B4 6F F1 58 07 1F EC C7 2C 6%..T...o.X....,
0040: 11 C6 2A 96 73 0F 99 70 AA D7 B9 51 77 57 31 95 ..*.s..p...QwW1.
0050: 8E B7 AC 24 72 89 AE BD A1 85 DF 97 F8 E7 E5 88 ...$r...........
0060: F1 1E 01 C2 E2 02 8E DA 34 66 B7 87 8E 05 98 DF ........4f......
0070: F7 54 94 21 ED AF 27 86 8B C3 4C ED 58 29 11 C8 .T.!..'...L.X)..
0080: 66 0C 29 24 1B 36 CD 9E 4E 20 BE D7 30 A7 D9 9B f.)$.6..N ..0...
0090: 17 A3 23 F3 30 CC 52 0B 86 D5 0B B4 2A 05 B3 01 ..#.0.R.....*...
00A0: 65 F1 AA D7 46 39 68 E6 53 C6 FB EA 75 02 F8 2D e...F9h.S...u..-
00B0: AB 0D 1A F8 4D 11 2A 86 71 F3 53 AD CE FB 70 5E ....M.*.q.S...p^
00C0: 26 5B 09 0D 6F E4 B2 CB 61 49 C6 C9 87 41 40 5E &[..o...aI...A@^
00D0: 30 93 41 9C F0 38 E0 D2 93 83 67 46 40 82 BA A6 0.A..8....gF@...
00E0: 09 AE 0E 0A C7 48 16 1B AE 3A 66 29 0A F0 4E DE .....H...:f)..N.
00F0: 49 83 BD 01 C0 83 70 5B F4 12 EC CF E1 8B F6 AE I.....p[........
0100: DE 4B 35 BF 3B D6 DC 79 0C 1B FE 68 CF 27 35 00 .K5.;..y...h.'5.
0110: 70 A9 91 CB E7 F2 53 3C 32 37 D1 AE 2A 21 17 D6 p.....S<27..*!..
0120: F3 CF 45 D1 A3 53 98 53 7C 36 BB 57 24 8B 8E 5C ..E..S.S.6.W$..\
0130: 08 46 20 6A 52 D1 17 B8 2F 1D 8A 5C 3C B3 21 A8 .F jR.../..\<.!.
0140: 38 A3 0B DE BB 9F 6E 3A 7B A7 61 DE 32 80 B3 A0 8.....n:..a.2...
0150: 87 AF 4C 5B F8 C7 13 B3 1F 02 3B 3E 46 C4 EB 94 ..L[......;>F...
0160: 6C B2 E2 F3 2E 7C 21 91 75 4A B6 19 B2 D1 FA B1 l.....!.uJ......
0170: D2 4F B4 27 17 7E FE 86 DF 77 E5 A9 1C EA 3A A9 .O.'.....w....:.
0180: C8 97 B5 E4 27 27 1C F3 7A 63 91 8A C1 CA 3B BC ....''..zc....;.
0190: A4 98 1F FB 99 F4 D9 43 A0 E2 C0 78 47 29 78 6C .......C...xG)xl
01A0: FF 11 8C 13 90 0D FF 7C 4D 7C 17 47 3B 2E F0 1A ........M..G;...
01B0: 2A 21 A7 44 D6 32 28 B9 16 08 1E 4E 33 32 B5 64 *!.D.2(....N32.d
01C0: DD C9 CB 6A 86 EC 16 41 DE 16 78 A9 53 74 69 E8 ...j...A..x.Sti.
01D0: 2F 20 80 F6 3F 53 46 49 D4 34 B1 35 A8 43 25 85 / ..?SFI.4.5.C%.
01E0: 9F 6C 38 B2 C7 25 F0 41 EA 4A 9B E2 C8 7A 2A 47 .l8..%.A.J...z*G
01F0: C9 F9 5C 15 14 27 C6 C7 80 F5 6F 18 6F 53 61 85 ..\..'....o.oSa.
]
Added certificate to keystore 'jssecacerts' using alias 'invako.kro.kr-1'
$ keytool -exportcert -keystore jssecacerts -storepass changeit -file output.cert -alias invako.kro.kr-1
Certificate stored in file <output.cert>
root@jenkins:/var/jenkins_home/cert#
$ keytool -importcert -keystore ${JAVA_HOME}/lib/security/cacerts -storepass changeit -file output.cert -alias letsencrypt
Warning: use -cacerts option to access cacerts keystore
Owner: CN=invako.kro.kr, OU=Personal, O=invako, L=Osong, ST=South, C=CN
Issuer: CN=invako.kro.kr, OU=Personal, O=invako, L=Osong, ST=Osong, C=CN
Serial number: 61365f30bf5c20760ddb9544bb5719d7e7dde459
Valid from: Thu Jan 11 23:53:50 UTC 2024 until: Sun Jan 08 23:53:50 UTC 2034
Certificate fingerprints:
SHA1: 50:E0:9D:5D:D1:E0:98:18:BB:E8:3C:82:7D:82:7E:B8:AF:8A:30:86
SHA256: 22:90:D9:9A:26:44:9B:9D:44:C9:61:90:6A:BF:F2:8C:C0:33:EB:5C:EC:4D:02:74:4A:9C:ED:EB:72:48:87:B4
Signature algorithm name: SHA512withRSA
Subject Public Key Algorithm: 4096-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 9D 39 8F 17 58 A9 81 00 9B A5 9C F1 01 44 60 09 .9..X........D`.
0010: A0 96 71 11 ..q.
]
]
#2: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[
CA:false
PathLen: undefined
]
#3: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
]
#4: ObjectId: 2.5.29.15 Criticality=false
KeyUsage [
DigitalSignature
Non_repudiation
Key_Encipherment
Data_Encipherment
]
#5: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: invako.kro.kr
]
#6: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 3C 64 12 AF C6 67 0B 58 C0 1D 10 E7 60 67 E1 1D <d...g.X....`g..
0010: 80 13 55 B7 ..U.
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore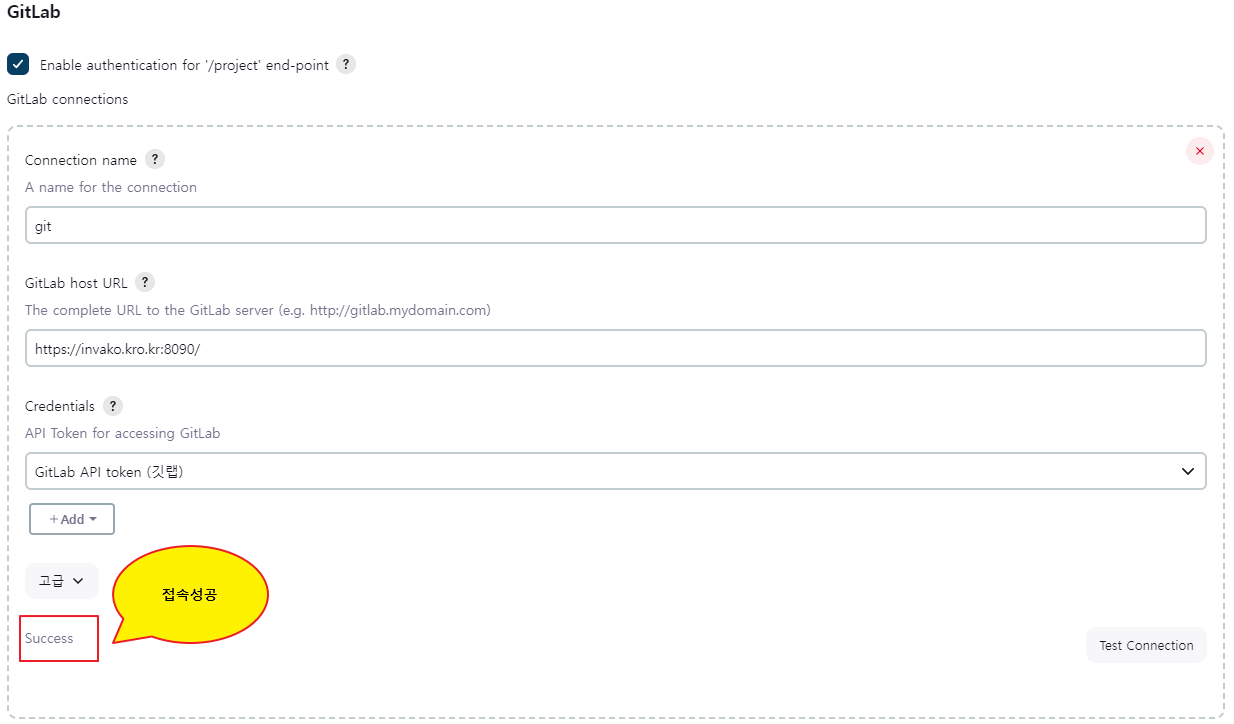
728x90
반응형